Building the Digital Trust Architecture: A Strategic Shift for 2026

In 2026, cybersecurity isn't just about keeping hackers out. It is about proving to your customers that their data is in a fortress. The conversation in the boardroom is shifting. For years, IT security was viewed purely as a cost center, a necessary insurance policy against potential disaster. As we look toward the future of digital business, that perspective is becoming obsolete.
Forward-thinking C-Suite executives and Compliance Officers are now pivoting toward a "Digital Trust" architecture. This approach positions your infrastructure not merely as a defensive wall, but as a verifiable asset that builds customer confidence and shortens sales cycles. When your security is transparent and robust, it becomes a competitive advantage. This paradigm shift from "never trust" to "continuously proven trust" is becoming critical for modern enterprises, especially given the complexities of expanding attack surfaces and AI-driven threats according to industry leaders.
The Evolution of the Trust Stack
A Digital Trust Architecture is not a single piece of software. It is an integrated ecosystem that validates identity and integrity at every touchpoint. For modern enterprises, particularly those moving towards 2026, this architecture is built on a specific triad of technologies: Azure Virtual Desktop (AVD), Microsoft Intune, and Entra ID (formerly Azure AD), aligning with broader strategic technology trends focusing on secure, scalable foundations for digital transformation as highlighted by Gartner.
At FlowDevs, we help organizations deploy this stack to create a seamless environment where security is inherent rather than bolted on.
- Entra ID: This acts as the universal passport. It governs who accesses what, ensuring that identity implementation is central to the architecture.
- Microsoft Intune: This manages the health of the devices accessing your data. If a device is not compliant with your security policies, it does not get in.
- Azure Virtual Desktop (AVD): This ensures that data never actually leaves your controlled environment. Employees stream the data rather than downloading it, keeping the "crown jewels" within your secure perimeter.
Zero Trust in a Remote-First World
The concept of the "office firewall" is dead. In a flexible work environment, the perimeter is no longer physical. It is digital. This is the core reality of Zero Trust. Your architecture must assume that every access attempt could be a threat until proven otherwise. While Zero Trust has been instrumental in reducing implicit trust, some implementations remain fragmented, focusing on isolated aspects like identity or network access PwC's 2026 Global Digital Trust Insights survey underscores the importance of a unified approach to digital trust.
When you utilize Entra ID alongside conditional access policies, you are essentially establishing the user's identity as the new perimeter. It does not matter if your CFO is working from headquarters or a hotel room in Tokyo. The security protocols travel with the identity, not the location. This flexibility is what allows modern businesses to scale without compromising on safety.
Compliance on Autopilot
For Compliance Officers, the Digital Trust Architecture solves the perpetual headache of audit preparation. Traditional compliance often involves manual log-checking and reactive patching. By integrating intelligent automation and cloud infrastructure, compliance becomes a byproduct of the system rather than a separate task. Indeed, the C-suite and boards are increasingly recognizing the necessity of embedding trust into their digital transformation agendas, moving beyond mere compliance as echoed in the PwC 2026 Global Digital Trust Insights for senior management.
When your environment is built on this modern stack, you automatically satisfy rigorous requirements for frameworks like HIPAA and CMMC. Features such as data residency controls, automatic session time-outs, and device encryption are enforcing policies 24/7 without human intervention. This shift reduces the administrative burden on your team and eliminates human error.
Turning Infrastructure into Value
Investing in this architecture is an investment in efficiency. When you streamline complex workflows through intelligent automation, you free your teams to focus on innovation rather than access management. At FlowDevs, we specialize in unlocking this efficiency. From building scalable cloud infrastructure to implementing Power Automate solutions, we ensure your technical vision drives real-world results. This strategic approach aligns with priorities identified for CISOs in 2026, which emphasize not just security, but also its role in enabling business objectives according to PwC.
It is time to stop viewing security as a barrier and start viewing it as a bridge to your customers. If you are ready to transition your organization from simple defense to a comprehensive Digital Trust Architecture, we can help guide the way.
Ready to assess your standing?
Download our "Digital Trust" checklist to see if your infrastructure is creating value or just reducing risk. To discuss a custom strategy for your organization, visit our bookings page to schedule a consultation with our team.
In 2026, cybersecurity isn't just about keeping hackers out. It is about proving to your customers that their data is in a fortress. The conversation in the boardroom is shifting. For years, IT security was viewed purely as a cost center, a necessary insurance policy against potential disaster. As we look toward the future of digital business, that perspective is becoming obsolete.
Forward-thinking C-Suite executives and Compliance Officers are now pivoting toward a "Digital Trust" architecture. This approach positions your infrastructure not merely as a defensive wall, but as a verifiable asset that builds customer confidence and shortens sales cycles. When your security is transparent and robust, it becomes a competitive advantage. This paradigm shift from "never trust" to "continuously proven trust" is becoming critical for modern enterprises, especially given the complexities of expanding attack surfaces and AI-driven threats according to industry leaders.
The Evolution of the Trust Stack
A Digital Trust Architecture is not a single piece of software. It is an integrated ecosystem that validates identity and integrity at every touchpoint. For modern enterprises, particularly those moving towards 2026, this architecture is built on a specific triad of technologies: Azure Virtual Desktop (AVD), Microsoft Intune, and Entra ID (formerly Azure AD), aligning with broader strategic technology trends focusing on secure, scalable foundations for digital transformation as highlighted by Gartner.
At FlowDevs, we help organizations deploy this stack to create a seamless environment where security is inherent rather than bolted on.
- Entra ID: This acts as the universal passport. It governs who accesses what, ensuring that identity implementation is central to the architecture.
- Microsoft Intune: This manages the health of the devices accessing your data. If a device is not compliant with your security policies, it does not get in.
- Azure Virtual Desktop (AVD): This ensures that data never actually leaves your controlled environment. Employees stream the data rather than downloading it, keeping the "crown jewels" within your secure perimeter.
Zero Trust in a Remote-First World
The concept of the "office firewall" is dead. In a flexible work environment, the perimeter is no longer physical. It is digital. This is the core reality of Zero Trust. Your architecture must assume that every access attempt could be a threat until proven otherwise. While Zero Trust has been instrumental in reducing implicit trust, some implementations remain fragmented, focusing on isolated aspects like identity or network access PwC's 2026 Global Digital Trust Insights survey underscores the importance of a unified approach to digital trust.
When you utilize Entra ID alongside conditional access policies, you are essentially establishing the user's identity as the new perimeter. It does not matter if your CFO is working from headquarters or a hotel room in Tokyo. The security protocols travel with the identity, not the location. This flexibility is what allows modern businesses to scale without compromising on safety.
Compliance on Autopilot
For Compliance Officers, the Digital Trust Architecture solves the perpetual headache of audit preparation. Traditional compliance often involves manual log-checking and reactive patching. By integrating intelligent automation and cloud infrastructure, compliance becomes a byproduct of the system rather than a separate task. Indeed, the C-suite and boards are increasingly recognizing the necessity of embedding trust into their digital transformation agendas, moving beyond mere compliance as echoed in the PwC 2026 Global Digital Trust Insights for senior management.
When your environment is built on this modern stack, you automatically satisfy rigorous requirements for frameworks like HIPAA and CMMC. Features such as data residency controls, automatic session time-outs, and device encryption are enforcing policies 24/7 without human intervention. This shift reduces the administrative burden on your team and eliminates human error.
Turning Infrastructure into Value
Investing in this architecture is an investment in efficiency. When you streamline complex workflows through intelligent automation, you free your teams to focus on innovation rather than access management. At FlowDevs, we specialize in unlocking this efficiency. From building scalable cloud infrastructure to implementing Power Automate solutions, we ensure your technical vision drives real-world results. This strategic approach aligns with priorities identified for CISOs in 2026, which emphasize not just security, but also its role in enabling business objectives according to PwC.
It is time to stop viewing security as a barrier and start viewing it as a bridge to your customers. If you are ready to transition your organization from simple defense to a comprehensive Digital Trust Architecture, we can help guide the way.
Ready to assess your standing?
Download our "Digital Trust" checklist to see if your infrastructure is creating value or just reducing risk. To discuss a custom strategy for your organization, visit our bookings page to schedule a consultation with our team.
Related Blog Posts

Google Workspace vs. Microsoft 365: The 2026 License Landscape
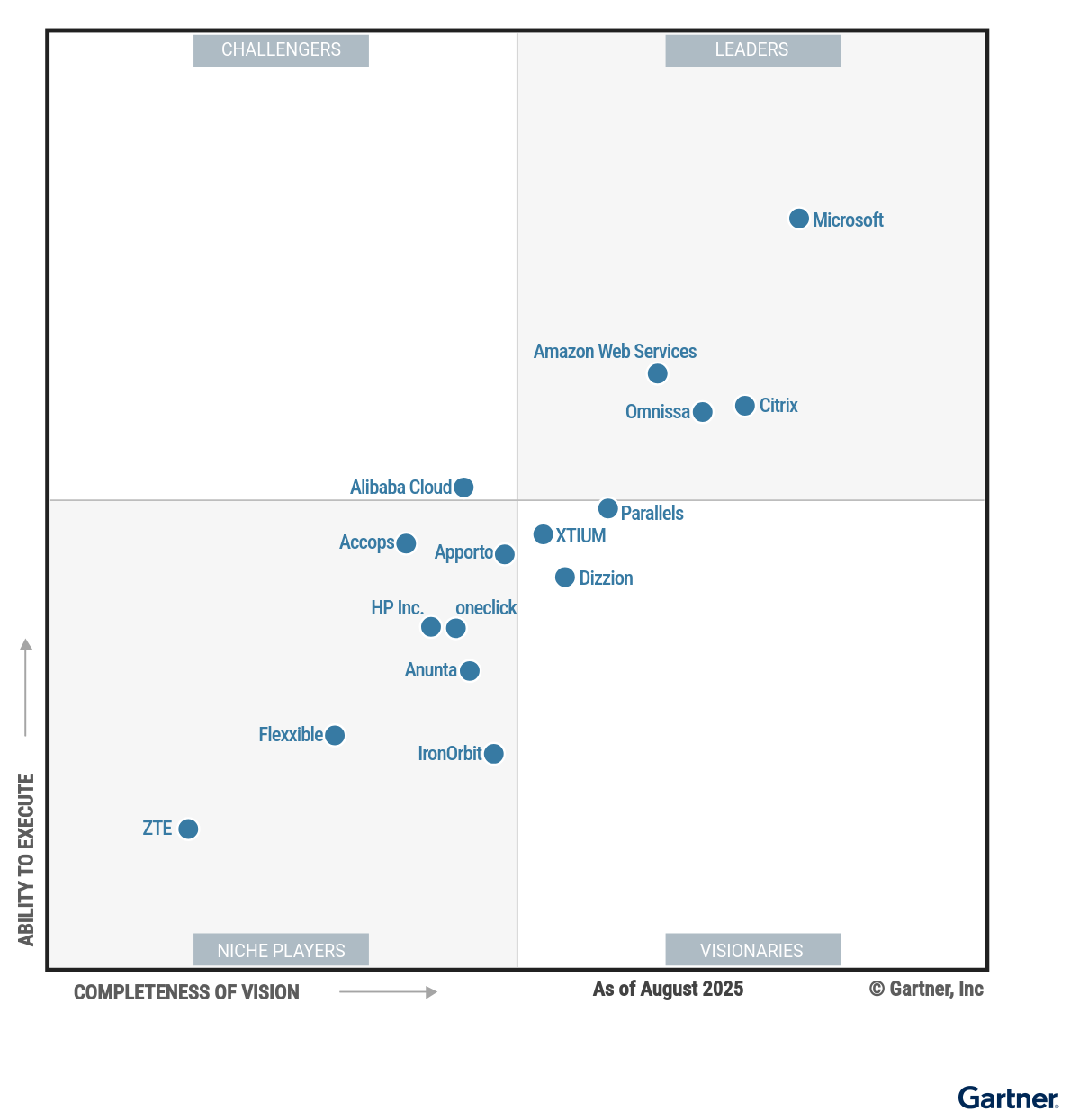
Key Takeaways from the 2025 Gartner Magic Quadrant for Desktop as a Service


.jpg)